Insecurity News |
| krb5 |
|
Kerberos is a networked authentication system that uses a trusted third party (a KDC) to authenticate clients and servers to each other. The krb5-workstation package includes a Kerberos-aware telnet client. Two buffer overflow flaws were discovered in the way the telnet client handles messages from a server. An attacker may be able to execute arbitrary code on a victim's machine if the victim can be tricked into connecting to a malicious telnet server. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the names CAN-2005-0468 and CAN-2005-0469 to these issues. Debian reference: DSA-703-1 krb5 Gentoo reference: GLSA 200504-04 / telnet Mandriva reference: MDKSA-2005:061 Red Hat reference: RHSA-2005:330-06 |
| MySQL |
|
MySQL is a multi-user, multi-threaded SQL database server. Stefano Di Paola discovered two bugs in the way MySQL handles user-defined functions. A user with the ability to create and execute a user defined function could potentially execute arbitrary code on the MySQL server. The CVE project has assigned the names CAN-2005-0709 and CAN-2005-0710 to these issues. Stefano Di Paola also discovered a bug in the way MySQL creates temporary tables. A local user could create a specially crafted symlink which could result in the MySQL server overwriting a file. The CVE project has assigned the name CAN-2005-0711 to this issue. Gentoo reference: GLSA 200503-19 / mysq Mandriva reference: MDKSA-2005:060 Red Hat reference: RHSA-2005:334-07 Suse reference: SUSE-SA:2005:019 |
| Telnet |
|
The telnet package provides a command line telnet client. The telnet-server package includes a telnet daemon, telnetd, that supports remote login to the host machine. Two buffer overflow flaws were discovered in the way the telnet client handles messages from a server. An attacker may be able to execute arbitrary code on a victim's machine if the victim can be tricked into connecting to a malicious telnet server. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the names CAN-2005-0468 and CAN-2005-0469 to these issues. Debian reference: DSA-703-1 krb5 Gentoo reference: GLSA 200504-04 / telnet Red Hat reference: RHSA-2005:327-10 |
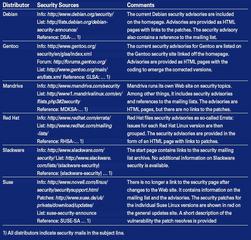
| Security Posture Of Major Distribution |
|

|
| Mozilla |
|
Mozilla is an open source Web browser, email and newsgroup client, IRC chat client, and HTML editor. A buffer overflow bug was found in the way Mozilla processes GIF images. It is possible for an attacker to create a specially crafted GIF image, which when viewed by a victim will execute arbitrary code as the victim. The CVE project has assigned the name CAN-2005-0399 to this issue. A bug was found in the way Mozilla displays dialog windows. It is possible that a malicious web page which is being displayed in a background tab could present the user with a dialog window appearing to come from the active page. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2004-1380 to this issue. A bug was found in the way Mozilla allowed plug-ins to load privileged content into a frame. It is possible that a malicious webpage could trick a user into clicking in certain places to modify configuration settings or execute arbitrary code. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2005-0232 to this issue. A bug was found in the way Mozilla Mail handles cookies when loading content over HTTP regardless of the user's preference. It is possible that a particular user could be tracked through the use of malicious mail messages which load content over HTTP. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2005-0149 to this issue. A bug was found in the way Mozilla responds to proxy auth requests. It is possible for a malicious webserver to steal credentials from a victim's browser by issuing a 407 proxy authentication request. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2005-0147 to this issue. A bug was found in the way Mozilla handles certain start tags followed by a NULL character. A malicious web page could cause Mozilla to crash when viewed by a victim. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2004-1613 to this issue. A bug was found in the way Mozilla sets file permissions when installing XPI packages. It is possible for an XPI package to install some files world readable or writable, allowing a malicious local user to steal information or execute arbitrary code. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2004-0906 to this issue. A bug was found in the way Mozilla loads links which are middle clicked in a new tab. A malicious web page could read local files or modify privileged chrom settings. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2005-0141 to this issue. A bug was found in the way Mozilla displays the secure site icon. A malicious web page can use a view-source URL targetted at a secure page, while loading an insecure page, yet the secure site icon shows the previous secure state. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2005-0144 to this issue. Gentoo reference: GLSA 200503-30 / Mozilla Red Hat reference: RHSA-2005:323-10 |
| gtk2 |
|
The gtk2 package contains the GIMP ToolKit (GTK+), a library for creating graphical user interfaces for the X Window System. A bug was found in the way gtk2 processes BMP images. It is possible that a specially crafted BMP image could cause a denial of service attack on applications linked against gtk2. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CAN-2005-0891 to this issue. Mandriva reference: MDKSA-2005:068 Red Hat reference: RHSA-2005:344-03 |